Identity crisis, or how not to implement RFID - written by NiXijav on 2020-08-23
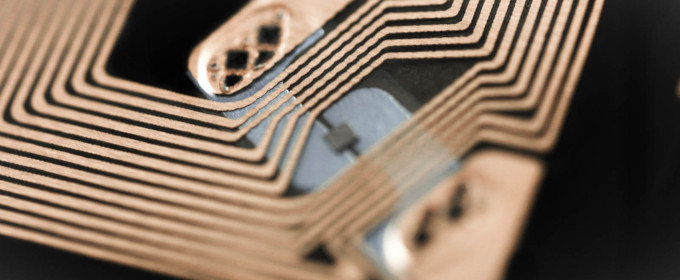
Some days ago, a place I usually frequent gave everyone an RFID access card. Security and convenience were the reasons given, but none of those was true.
TL;DR: Don't use Mifare UIDs to authenticate users, they are easily spoofed.Let's dive into a little investigation about the real security of this system. The first thing I did was scan the tag with my phone. Sure enough, with NFC Tools on Android, this is what appeared:
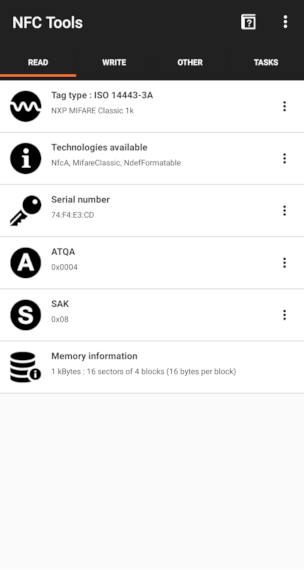
This is a Mifare Classic 1K Card, and it seems to be empty! Let's confirm this with another Android app, MIFARE Classic Tool. Reading a tag from this app is simple, Read Tag and then Start Mapping and Read Tag. And again, sure enough, the tag is empty. Could this mean they are using the card UID (serial number field in previous picture) to identify each user?
Pay special attention to the first line, the one in purple:

Also, as you may know, Mifare cards have different keys for different blocks. But as we just saw, security here is nonexistent, as all the keys are the default ones (FFFFFFFFFFFF, text in light and dark green). The conclusion is clear: they are using the card's unique ID as the user identifier. This is catastrophic because of three reasons:
- Not all users can access all places.
- With the default keys and only the UID as the identifier, card cloning is trivial.
- One can scan another user card to find other UIDs.
Time to clone our card and try it out. If you try to modify the UID on block 0 of your card (or the whole block for that matter), chances are it won't work. On genuine MiFare tags, block 0 is non-writable.
If you look closely on Chinese websites (can't give you any more clues or this would pose no challenge for you), you'll be able to find block 0 writable tags. These clones work identically as their original counterparts.
I haven't found an app yet able to write to these cards (they have a backdoor to enable block 0 writing), but an Arduino with the MFRC522 module and the RFID library will do. There's already an example sketch called ChangeUID, but for some reason, it didn't work for me. Using another example sketch as a reference (FixBrickedUID), I successfully wrote block 0. The code I used is available in this Gist.
I copied and wrote block 0 from the original card (purple text on the previous image) to the Chinese one. After verifying both cards were identical, it was time to test our clone.
And of course... it worked 🤦â€â™‚ï¸
P.S. Except for block 0, you can write to the rest of the original card. NFC Tools allows you to write different things like URLs and YouTube videos. If scanned with a smartphone, this content would pop up, and the door would still open normally. Quick idea: rickroll everyone (yes I tried, and yes it worked wonderfully 🕺).
No comments yet
Leave a comment